Hackers are more economical today, so it’s necessary to employ efficient IT security applications that could protect against personal computer internet dangers.
Online fraudsters aim at resisting or damaging the hardware, electronics, or software data.
Since the dawn of the Web of Things and the growth of cloud-based businesses (big & little ), we have confronted increased vulnerabilities. Another reason might be that they have been not as monolithic, heritage architectures, and more distributed, microservice-based networks.
In general, computers play an essential part in the management of most businesses. If IT security computer software fails, every section of this business is going to be exposed to online dangers. In situations like this, it’s very likely to affect productivity, customers, and profits experience; therefore, customers can also elect different businesses.
Together with those things going on on the desktop – financial losses will increase by the moment. Never forget, that IT Security isn’t merely the first parameter; it may lead to havoc if not chosen carefully. Besides that, additionally, it requires revisiting at fixed intervals.
You May Read: RapidSSL Wildcard Certificate
Within the following column, we will research Security versus cyber Security versus Network Security and what is the ideal tech for organizations throughout the planet. With all these tips, arm your system with the appropriate persons and plans to boost your defense and keep risks away!
Types of Security:-
- IT Security
- Cyber-security
- Network Security
IT Security
IT security is precisely about”data security.”The IT security pro will concentrate on the ethics, integrity, and access to {the|this} data. At the current time, many quantities of data remain from PCs, laptops, computers, or somewhere online.
Nevertheless, while in the late ’90s, until most sensitive data was moved online, it had been sitting in a filing cabinet. Now, IT security applications are included with ensuring data of virtually any sort is kept secure and can be just a little wider than cybersecurity. Thus, necessarily an IT security expert does not have to be a cybersecurity expert.
IT Solutions, share our ideas and provenly profit your business and online presence too. Apart from the perfectly designed websites, the most important thing is the functional and responsive website.
The further links in a system’s series, the more, the higher the chances for hackers to discover their manner. Each component requires its subsequent security measures–together with a number of them overlapping and working in tandem, much like the real elements of a network perform.
Besides, it is essential to be aware that together with security, there is no one-size-fits-all solution. Every network differs and requires trained professionals to create tailored plans around all of the arenas: programs, databases, media devices and media hosts, IT infrastructures, and also the usually weakest link in the security series: users. These security plans are alive, breathing things that will need to be upgraded, updated, and adjusted continuously, too.
Cybersecurity
Besides the simple fact that it is all about protecting the data that resides within the electronic kind. One other element of this will be to recognize what the vital information is, where it lives, and also the measures that will need to be executed to protect it.
From the procedure, cyber-security is bound to shield a company’s networks, networks, and data in bogus electronic access, vandalism, or assault from incorporating several technologies, procedures, and regulations.
Cybersecurity is significant because government, corporate, military, financial, and healthcare companies collect, process, and save unprecedented levels of data on computers and different apparatus.

An essential part of the data might be sensitive data that’s intellectual property, financial data, personal data, or different kinds of data that unauthorized access or vulnerability might have adverse effects.
Companies transmit sensitive data across networks and also to other apparatus in the plan of doing organizations, and cyber-security identifies the area focused on protecting that information as well as the procedures used to store or process it.
There are multiple ways to protect in-transit and physical data. For the protection of data transmission between the server and the user, the best SSL certificate from Cheapsslshop could be a better way. It ensures that the data flows between both ends are end-to-end encrypted. A website should have an SSL certificate to keep cyber culprits away from ongoing data.
As the sophistication and volume of cyberattacks grow, businesses and associations, particularly the ones that can be tasked with protecting information concerning domestic security, health, or economic records, want to take action to secure their sensitive company and employees’ advice.
Network Security
The system security attempts to protect the information delivered through various devices within the company network. It is aimed at making sure the information isn’t intercepted or changed. Therefore, it’s the responsibility of their network security to safeguard IT infrastructure from all kinds of threats, including viruses, worms, Trojans, zero-day, spyware strikes, and much more.
A perfect network security in a position does not just ensure security but also assists in recognizing new threats before they infiltrate a system and even endanger the information. The Frequent safety Elements of network safety comprise firewalls, anti-virus applications intrusion detection and avoidance methods (IDS/IPS), and virtual private networks (VPN).
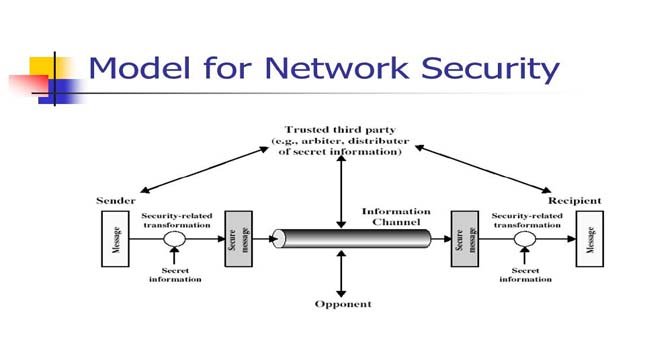
Network security isn’t anything you do to secure your system, both the hardware and applications. Network administrators (or network administrators) are accountable for ensuring the reliability, usability, and ethics of one’s system remains complete. A hacker is capable of becoming a system and obstructing your access, such as by merely holding a {system|method} hostage to get a BitCoin ransom. You want a superb defense setup to make sure you are protected.
The tradition of avoiding such dangers by building systems to be more safe, dependable, and protected from malicious attacks. Security engineers design systems from the bottom up, protecting the appropriate items in the proper ways. When an application engineer’s objective is always to ensure things do happen (click here, and this also happens), a security engineer aims to make sure things do not occur by designing, executing, and analyzing secure and complete systems.
The Way to Secure Network from Cyber Attacks
Thus, the usage of most three experts is emerging tremendously to safeguard data appropriately. The demand for this particular issue is becoming more commonplace in these times, on account of the businesses, and customers have begun to do a check-up on the latest technologies. it’s very own effective measures in securing handling and data hazards in both cyber and physical breeds.
From the extended duration, it’s clear that cyber attacks will probably soon be far more complicated and complicated. Yet, new technologies may give a better possibility of fighting those cyber attacks. Anyway, it only provides a high level of service for the customers.
Comodo ONE could be the finest at a class product that might assist you in accomplishing your own IT security goals economically. This will allow you to get into an entirely functional IT system contributing to optimizing operational efficiencies, improved employee morale, happy clients, and ultimately skyrocketing profits.
The Very Most Effective IT Security Provider in the United States
As demonstrated by a cyber-security Ventures report, it’ll cost businesses roughly $6 billion annually from 2024 as a result of this growing cybercrime. The task is enormous, thereby, an increasing number of organizations are putting forth their utmost efforts in combating cyber threats/attacks.
The set of businesses that manage cybersecurity, network security, and IT security applications is overly long-term. But if you’re taking a look at something trendy, practical, and powerful that could combat security problems on all fronts afterward, Comodo ONE can be the perfect option.
IT company in Malaysia focuses on understanding client requirements, challenges, and technology goals which form the foundation of our customer-centric solutions. It packs all you will need to handle your organization. In other words, it lets you develop the enterprise and increase your clientele while resolving the clients’ IT challenges proactively.
The centralized console enables you to manage all without difficulty. Its MSP infrastructure comprises an integral service that fosters the earnings. It is possible to provide subscription-based services to your clients and manage them directly out of one pane of glass and supply endpoint security, web security, data backup, and network tracking and security.

